The scanning process
Snow Inventory Oracle Scanner is designed to perform automatic Oracle inventory without the need to create a specific user account within the Oracle databases. The scanner automatically discovers all running Oracle instances on the current server, detects what user is running each database instance, and switches to that specific user when inventorying the databases. No specific permissions and no specific user is needed to inventory the databases.
The scanner is designed to be lightweight and scalable regarding size and number of objects in database. Resource consumption is mainly CPU bound as metadata is often available in memory.
Performing only read operations on databases, the scanner has been designed in a non-invasive manner. It performs SELECT queries based on PL/SQL blocks to extract the inventory data needed to determine license needs.
Only Oracle internal objects listed in Required Oracle permissions are accessed. To avoid concerns related to data security, the scanner never reads user or application data.
Flexera recommends the use of automatic Oracle Inventory rather than setting up specific user accounts and permissions for each Oracle database.
All inventory results provide a snapshot of the environment from the time when the inventory scan was performed.
Oracle inventory with specific user authentication, simplified config
If you do not wish to use automatic Oracle Inventory, it is possible to use the scanner with a specific user.
To avoid the time-consuming process of creating this user with specific SELECT permissions, the user account can be created with SELECT permissions on ALL TABLES and DICTIONARY in all databases. The account also needs to be able to CREATE SESSION, by granting the user SELECT ANY privileges on TABLE and DICTIONARY, see the example below.
The user needs to be created and permissions need to be granted on each database that is to be inventoried.
EXAMPLE
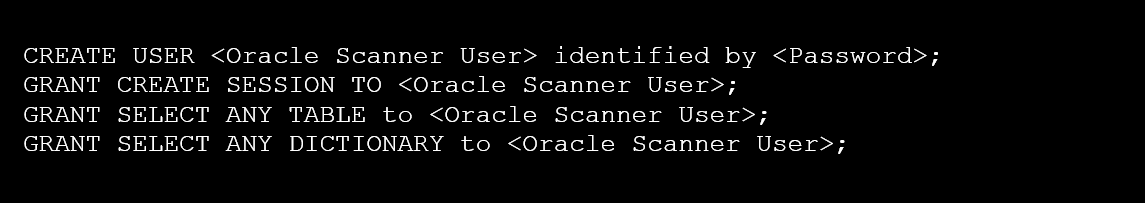
Create the user <Oracle Scanner User> and grant SELECT ANY privileges in earlier versions than Oracle 12c:
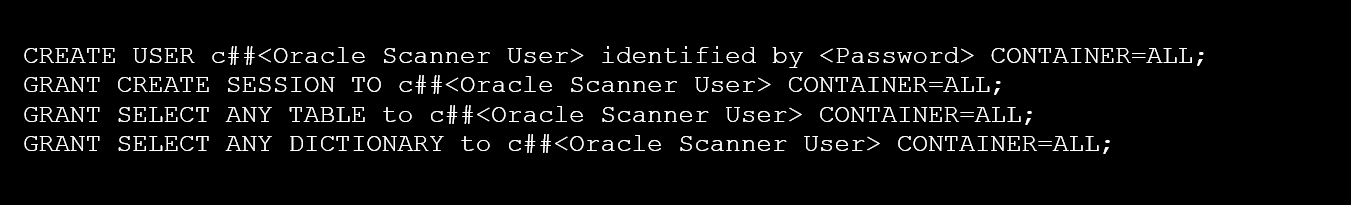
For Oracle version 12c or later, the user needs to be created as a common user, by typing c## before the username. Also, CONTAINER=ALL must be added to each line, see the example below.
EXAMPLE
Create the user <Oracle Scanner User> and grant SELECT ANY privileges in Oracle 12c or later:
Required Oracle permissions
The list below details the objects accessed during the Oracle inventory, and so the user needs to be able to run SELECT queries on these tables/views. If Oracle built-in roles and privileges cannot be used due to security reasons, grants need to be made to the objects listed here.
| all_sdo_geom_metadata | all_views |
| cdb_pdb_history | dba_advisor_tasks |
| dba_aws | dba_cpu_usage_statistics |
| dba_cubes | dba_encrypted_columns |
| dba_feature_usage_statistics | dba_flashback_archive |
| dba_flashback_archive_tables | dba_flashback_archive_ts |
| dba_indexes | dba_lob_partitions |
| dba_lob_subpartitions | dba_lobs |
| dba_object_tables | dba_objects |
| dba_recyclebin | dba_registry |
| dba_segments | dba_sql_profiles |
| dba_sqlset | dba_sqlset_references |
| dba_tab_columns | dba_tab_partitions |
| dba_tab_subpartitions | dba_tables |
| dba_tablespaces | dba_users |
| dba_workload_captures | dba_workload_filters |
| dba_workload_replays | dmsys.dm$model |
| dmsys.dm$object | dmsys.dm$p_model |
| dual | dvsys.dba_dv_realm |
| dvsys.dba_dv_realm_auth | global_name |
| gv$im_segments | gv$instance |
| gv$parameter | lbacsys.lbac$polt |
| lbacsys.ols$polt | mdsys.sdo_feature_usage |
| mdsys.sdo_geom_metadata_table | mgmt$target |
| mgmt_targets | odm.odm_mining_model |
| odm_document | odm_record |
| olapsys.dba$olap_cubes | RC_DATABASE |
| redaction_policies | sys.cdc_change_sets$ |
| sys.cdc_change_tables$ | sys.dba_mining_models |
| sys.dba_users | sys.model$ |
| sys.obj$ | sys.registry$history |
| sysman.mgmt_admin_licenses | sysman.mgmt_fu_license_map |
| sysman.mgmt_fu_registrations | sysman.mgmt_fu_statistics |
| sysman.mgmt_inv_component | sysman.mgmt_inv_container |
| sysman.mgmt_license_confirmation | sysman.mgmt_license_definitions |
| sysman.mgmt_licensed_targets | sysman.mgmt_licenses |
| sysman.mgmt_target_types | sysman.mgmt_targets |
| sysman.mgmt_versions | system.aq$_queue_tables |
| system.aq$_queues | system.fnd_oracle_userid |
| system.product_privs | system.schema_version_registry |
| timesten.tt_gridid | timesten.tt_gridinfo |
| user_role_privs | v$archive_dest_status |
| v$block_change_tracking | v$containers |
| v$database | v$dataguard_config |
| v$instance | v$license |
| v$option | v$parameter |
| v$pdbs | v$session |
| v$session_connect_info | v$version |
If E-Business Suite inventory is enabled, permissions on the following objects are also needed:
| apps.ad_applied_patches | apps.ap_invoices_all |
| apps.ben_prtt_enrt_rslt_f | apps.cn_srp_plan_assigns_all |
| apps.fnd_application | apps.fnd_application_tl |
| apps.fnd_form_functions | apps.fnd_form_functions_tl |
| apps.fnd_login_responsibilities | apps.fnd_logins |
| apps.fnd_menu_entries | apps.fnd_menu_entries_tl |
| apps.fnd_menus | apps.fnd_menus_tl |
| apps.fnd_nodes | apps.fnd_product_groups |
| apps.fnd_product_installations | apps.fnd_profile_option_values |
| apps.fnd_profile_options | apps.fnd_resp_functions |
| apps.fnd_responsibility | apps.fnd_responsibility_tl |
| apps.fnd_security_groups | apps.fnd_user |
| apps.fnd_user_resp_groups | apps.fnd_user_resp_groups_all |
| apps.fnd_user_responsibility | apps.hr_legislation_installations |
| apps.hr_person_type_usage_info | apps.hxc_time_building_blocks |
| apps.hxc_timecard_summary | apps.icx_sessions |
| apps.oe_order_headers_all | apps.oe_order_lines_all |
| apps.oe_order_sources | apps.per_addresses |
| apps.per_all_people_f | apps.per_contracts_f |
| apps.per_person_type_usages_f | apps.per_person_types |
| apps.per_person_types_tl | apps.po_requisition_headers_all |
| apps.po_requisition_lines_all | apps.poa_edw_po_dist_f |
| apps.qp_util | apps.wf_local_user_roles |
| apps.wf_user_role_assignments | ota.ota_delegate_bookings |
The default database schema for Oracle E-Business Suite is APPS. If you configured E-Business Suite on another database schema, please use that schema when granting the required permissions.
Examples: Required Oracle permissions
In this scenario, the Oracle built-in roles and privileges cannot be used due to security reasons.
The following example script creates the user OSCAN, and then adds the required Oracle permissions, which are used for non-container databases:
CREATE USER OSCAN IDENTIFIED BY <passwd>;
GRANT CREATE SESSION TO OSCAN;
GRANT EXECUTE ON SYS.DBMSOUTPUT_LINESARRAY TO OSCAN;
GRANT EXECUTE ON SYS.DBMS_APPLICATION_INFO TO OSCAN;
GRANT EXECUTE ON SYS.DBMS_OUTPUT TO OSCAN;
GRANT SELECT ON DBA_INDEXES TO OSCAN;
GRANT SELECT ON DMSYS.DM$MODEL TO OSCAN;
GRANT SELECT ON DMSYS.DM$OBJECT TO OSCAN;
GRANT SELECT ON DMSYS.DM$P_MODEL TO OSCAN;
GRANT SELECT ON DVSYS.DBA_DV_REALM TO OSCAN;
GRANT SELECT ON DVSYS.DBA_DV_REALM_AUTH TO OSCAN;
GRANT SELECT ON GV_$IM_SEGMENTS TO OSCAN;
GRANT SELECT ON LBACSYS.LBAC$POLT TO OSCAN;
GRANT SELECT ON LBACSYS.OLS$POLT TO OSCAN;
GRANT SELECT ON MDSYS.ALL_SDO_GEOM_METADATA TO OSCAN;
GRANT SELECT ON MDSYS.SDO_FEATURE_USAGE TO OSCAN;
GRANT SELECT ON MDSYS.SDO_GEOM_METADATA_TABLE TO OSCAN;
GRANT SELECT ON MGMT$TARGET TO OSCAN;
GRANT SELECT ON ODM.ODM_MINING_MODEL TO OSCAN;
GRANT SELECT ON ODM_DOCUMENT TO OSCAN;
GRANT SELECT ON ODM_RECORD TO OSCAN;
GRANT SELECT ON OLAPSYS.DBA$OLAP_CUBES TO OSCAN WITH GRANT OPTION;
GRANT SELECT ON RC_DATABASE TO OSCAN;
GRANT SELECT ON SYS.ALL_VIEWS TO OSCAN;
GRANT SELECT ON SYS.CDB_PDB_HISTORY TO OSCAN;
GRANT SELECT ON SYS.CDC_CHANGE_SETS$ TO OSCAN;
GRANT SELECT ON SYS.CDC_CHANGE_TABLES$ TO OSCAN;
GRANT SELECT ON SYS.DBA_ADVISOR_TASKS TO OSCAN;
GRANT SELECT ON SYS.DBA_AWS TO OSCAN;
GRANT SELECT ON SYS.DBA_CPU_USAGE_STATISTICS TO OSCAN;
GRANT SELECT ON SYS.DBA_CUBES TO OSCAN;
GRANT SELECT ON SYS.DBA_ENCRYPTED_COLUMNS TO OSCAN;
GRANT SELECT ON SYS.DBA_FEATURE_USAGE_STATISTICS TO OSCAN;
GRANT SELECT ON SYS.DBA_FLASHBACK_ARCHIVE TO OSCAN;
GRANT SELECT ON SYS.DBA_FLASHBACK_ARCHIVE_TABLES TO OSCAN;
GRANT SELECT ON SYS.DBA_FLASHBACK_ARCHIVE_TS TO OSCAN;
GRANT SELECT ON SYS.DBA_LOB_PARTITIONS TO OSCAN;
GRANT SELECT ON SYS.DBA_LOB_SUBPARTITIONS TO OSCAN;
GRANT SELECT ON SYS.DBA_LOBS TO OSCAN;
GRANT SELECT ON SYS.DBA_MINING_MODELS TO OSCAN;
GRANT SELECT ON SYS.DBA_OBJECT_TABLES TO OSCAN;
GRANT SELECT ON SYS.DBA_OBJECTS TO OSCAN;
GRANT SELECT ON SYS.DBA_RECYCLEBIN TO OSCAN;
GRANT SELECT ON SYS.DBA_REGISTRY TO OSCAN;
GRANT SELECT ON SYS.DBA_SEGMENTS TO OSCAN;
GRANT SELECT ON SYS.DBA_SQL_PROFILES TO OSCAN;
GRANT SELECT ON SYS.DBA_SQLSET_REFERENCES TO OSCAN;
GRANT SELECT ON SYS.DBA_SQLSET TO OSCAN;
GRANT SELECT ON SYS.DBA_TAB_COLUMNS TO OSCAN;
GRANT SELECT ON SYS.DBA_TAB_PARTITIONS TO OSCAN;
GRANT SELECT ON SYS.DBA_TAB_SUBPARTITIONS TO OSCAN;
GRANT SELECT ON SYS.DBA_TABLES TO OSCAN;
GRANT SELECT ON SYS.DBA_TABLESPACES TO OSCAN;
GRANT SELECT ON SYS.DBA_USERS TO OSCAN;
GRANT SELECT ON SYS.DBA_WORKLOAD_CAPTURES TO OSCAN;
GRANT SELECT ON SYS.DBA_WORKLOAD_FILTERS TO OSCAN;
GRANT SELECT ON SYS.DBA_WORKLOAD_REPLAYS TO OSCAN;
GRANT SELECT ON SYS.DUAL TO OSCAN;
GRANT SELECT ON SYS.GLOBAL_NAME TO OSCAN;
GRANT SELECT ON SYS.GV_$INSTANCE TO OSCAN;
GRANT SELECT ON SYS.GV_$PARAMETER TO OSCAN;
GRANT SELECT ON SYS.MODEL$ TO OSCAN;
GRANT SELECT ON SYS.OBJ$ TO OSCAN;
GRANT SELECT ON SYS.REDACTION_POLICIES TO OSCAN;
GRANT SELECT ON SYS.REGISTRY$HISTORY TO OSCAN;
GRANT SELECT ON SYS.USER_ROLE_PRIVS TO OSCAN;
GRANT SELECT ON SYS.V_$ARCHIVE_DEST_STATUS TO OSCAN;
GRANT SELECT ON SYS.V_$BLOCK_CHANGE_TRACKING TO OSCAN;
GRANT SELECT ON SYS.V_$CONTAINERS TO OSCAN;
GRANT SELECT ON SYS.V_$DATABASE TO OSCAN;
GRANT SELECT ON SYS.V_$DATAGUARD_CONFIG TO OSCAN;
GRANT SELECT ON SYS.V_$INSTANCE TO OSCAN;
GRANT SELECT ON SYS.V_$LICENSE TO OSCAN;
GRANT SELECT ON SYS.V_$OPTION TO OSCAN;
GRANT SELECT ON SYS.V_$PARAMETER TO OSCAN;
GRANT SELECT ON SYS.V_$PDBS TO OSCAN;
GRANT SELECT ON SYS.V_$SESSION TO OSCAN;
GRANT SELECT ON SYS.V_$SESSION_CONNECT_INFO TO OSCAN;
GRANT SELECT ON SYS.V_$VERSION TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_ADMIN_LICENSES TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_FU_LICENSE_MAP TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_FU_REGISTRATIONS TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_FU_STATISTICS TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_INV_COMPONENT TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_INV_CONTAINER TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_LICENSE_CONFIRMATION TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_LICENSE_DEFINITIONS TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_LICENSED_TARGETS TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_LICENSES TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_TARGET_TYPES TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_TARGETS TO OSCAN;
GRANT SELECT ON SYSMAN.MGMT_VERSIONS TO OSCAN;
GRANT SELECT ON SYSTEM.AQ$_QUEUE_TABLES TO OSCAN;
GRANT SELECT ON SYSTEM.AQ$_QUEUES TO OSCAN;
GRANT SELECT ON SYSTEM.FND_ORACLE_USERID TO OSCAN;
GRANT SELECT ON SYSTEM.PRODUCT_PRIVS TO OSCAN WITH GRANT OPTION;
GRANT SELECT ON SYSTEM.SCHEMA_VERSION_REGISTRY TO OSCAN;
GRANT SELECT ON TIMESTEN.TT_GRIDID TO OSCAN;
GRANT SELECT ON TIMESTEN.TT_GRIDINFO TO OSCAN;
If E-Business Suite scanning is enabled, the following example adds the required Oracle permissions for the user OSCAN. The default database schema for Oracle E-Business Suite is APPS. If you configured E-Business Suite on another database schema, make sure to apply the proper schema name on the example script as well.
GRANT SELECT ON APPS.AD_APPLIED_PATCHES TO OSCAN;
GRANT SELECT ON APPS.FND_APPLICATION TO OSCAN;
GRANT SELECT ON APPS.FND_APPLICATION_TL TO OSCAN;
GRANT SELECT ON APPS.FND_FORM_FUNCTIONS TO OSCAN;
GRANT SELECT ON APPS.FND_FORM_FUNCTIONS_TL TO OSCAN;
GRANT SELECT ON APPS.FND_LOGIN_RESPONSIBILITIES TO OSCAN;
GRANT SELECT ON APPS.FND_LOGINS TO OSCAN;
GRANT SELECT ON APPS.FND_MENU_ENTRIES TO OSCAN;
GRANT SELECT ON APPS.FND_MENU_ENTRIES_TL TO OSCAN;
GRANT SELECT ON APPS.FND_MENUS TO OSCAN;
GRANT SELECT ON APPS.FND_MENUS_TL TO OSCAN;
GRANT SELECT ON APPS.FND_PRODUCT_INSTALLATIONS TO OSCAN;
GRANT SELECT ON APPS.FND_RESP_FUNCTIONS TO OSCAN;
GRANT SELECT ON APPS.FND_RESPONSIBILITY TO OSCAN;
GRANT SELECT ON APPS.FND_RESPONSIBILITY_TL TO OSCAN;
GRANT SELECT ON APPS.FND_SECURITY_GROUPS TO OSCAN;
GRANT SELECT ON APPS.FND_USER TO OSCAN;
GRANT SELECT ON APPS.FND_USER_RESP_GROUPS TO OSCAN;
GRANT SELECT ON APPS.FND_USER_RESP_GROUPS_ALL TO OSCAN;
GRANT SELECT ON APPS.FND_USER_RESPONSIBILITY TO OSCAN;
GRANT SELECT ON APPS.ICX_SESSIONS TO OSCAN;
GRANT SELECT ON APPS.OE_ORDER_HEADERS_ALL TO OSCAN;
GRANT SELECT ON APPS.OE_ORDER_LINES_ALL TO OSCAN;
GRANT SELECT ON APPS.OE_ORDER_SOURCES TO OSCAN;
GRANT SELECT ON APPS.WF_LOCAL_USER_ROLES TO OSCAN;
GRANT SELECT ON APPS.WF_USER_ROLE_ASSIGNMENTS TO OSCAN;
GRANT SELECT ON APPS.PER_ALL_PEOPLE_F TO OSCAN;
GRANT SELECT ON APPS.HR_LEGISLATION_INSTALLATIONS TO OSCAN;
GRANT SELECT ON APPS.FND_PROFILE_OPTIONS TO OSCAN;
GRANT SELECT ON APPS.FND_PROFILE_OPTION_VALUES TO OSCAN;
GRANT SELECT ON APPS.FND_NODES TO OSCAN;
GRANT SELECT ON APPS.FND_PRODUCT_GROUPS TO OSCAN;
GRANT SELECT ON APPS.AP_INVOICES_ALL TO OSCAN;
GRANT SELECT ON APPS.PER_CONTRACTS_F TO OSCAN;
GRANT SELECT ON APPS.PER_PERSON_TYPES TO OSCAN;
GRANT SELECT ON APPS.BEN_PRTT_ENRT_RSLT_F TO OSCAN;
GRANT SELECT ON APPS.CN_SRP_PLAN_ASSIGNS_ALL TO OSCAN;
GRANT SELECT ON APPS.PO_REQUISITION_HEADERS_ALL TO OSCAN;
GRANT SELECT ON APPS.PO_REQUISITION_LINES_ALL TO OSCAN;
GRANT SELECT ON APPS.PER_ADDRESSES TO OSCAN;
GRANT SELECT ON OTA.OTA_DELEGATE_BOOKINGS TO OSCAN;
GRANT SELECT ON APPS.HXC_TIMECARD_SUMMARY TO OSCAN;
GRANT SELECT ON APPS.HXC_TIME_BUILDING_BLOCKS TO OSCAN;
GRANT SELECT ON APPS.POA_EDW_PO_DIST_F TO OSCAN;
GRANT SELECT ON APPS.PER_PERSON_TYPES_TL TO OSCAN;
GRANT SELECT ON APPS.PER_PERSON_TYPE_USAGES_F TO OSCAN;
GRANT EXECUTE ON APPS.QP_UTIL TO OSCAN;
GRANT EXECUTE ON APPS.HR_PERSON_TYPE_USAGE_INFO TO OSCAN;
The following example script creates the user C##OSCAN that needs to be created as a common user, and then adds the required Oracle permissions, which are used for container databases:
CREATE USER C##OSCAN IDENTIFIED BY <passwd> CONTAINER=ALL;
ALTER USER C##OSCAN SET CONTAINER_DATA=ALL CONTAINER=CURRENT;
GRANT CONNECT TO C##OSCAN CONTAINER=ALL;
GRANT CREATE SESSION TO C##OSCAN CONTAINER=ALL;
GRANT EXECUTE ON SYS.DBMSOUTPUT_LINESARRAY TO C##OSCAN CONTAINER=ALL;
GRANT EXECUTE ON SYS.DBMS_APPLICATION_INFO TO C##OSCAN CONTAINER=ALL;
GRANT EXECUTE ON SYS.DBMS_OUTPUT TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON DBA_INDEXES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON DMSYS.DM$MODEL TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON DMSYS.DM$OBJECT TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON DMSYS.DM$P_MODEL TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON DVSYS.DBA_DV_REALM TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON DVSYS.DBA_DV_REALM_AUTH TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON GV_$IM_SEGMENTS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON LBACSYS.LBAC$POLT TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON LBACSYS.OLS$POLT TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON MDSYS.ALL_SDO_GEOM_METADATA TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON MDSYS.SDO_FEATURE_USAGE TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON MDSYS.SDO_GEOM_METADATA_TABLE TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON MGMT$TARGET TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON ODM.ODM_MINING_MODEL TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON ODM_DOCUMENT TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON ODM_RECORD TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON OLAPSYS.DBA$OLAP_CUBES TO C##OSCAN WITH GRANT OPTION CONTAINER=ALL;
GRANT SELECT ON RC_DATABASE TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.ALL_VIEWS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.CDB_PDB_HISTORY TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.CDC_CHANGE_SETS$ TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.CDC_CHANGE_TABLES$ TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_ADVISOR_TASKS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_AWS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_CPU_USAGE_STATISTICS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_CUBES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_ENCRYPTED_COLUMNS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_FEATURE_USAGE_STATISTICS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_FLASHBACK_ARCHIVE TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_FLASHBACK_ARCHIVE_TABLES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_FLASHBACK_ARCHIVE_TS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_LOB_PARTITIONS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_LOB_SUBPARTITIONS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_LOBS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_MINING_MODELS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_OBJECT_TABLES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_OBJECTS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_RECYCLEBIN TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_REGISTRY TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_SEGMENTS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_SQL_PROFILES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_SQLSET TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_SQLSET_REFERENCES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_TAB_COLUMNS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_TAB_PARTITIONS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_TAB_SUBPARTITIONS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_TABLES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_TABLESPACES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_USERS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_WORKLOAD_CAPTURES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_WORKLOAD_FILTERS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DBA_WORKLOAD_REPLAYS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.DUAL TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.GLOBAL_NAME TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.GV_$INSTANCE TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.GV_$PARAMETER TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.MODEL$ TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.OBJ$ TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.REDACTION_POLICIES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.REGISTRY$HISTORY TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.USER_ROLE_PRIVS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$ARCHIVE_DEST_STATUS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$BLOCK_CHANGE_TRACKING TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$CONTAINERS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$DATABASE TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$DATAGUARD_CONFIG TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$INSTANCE TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$LICENSE TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$OPTION TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$PARAMETER TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$PDBS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$SESSION TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$SESSION_CONNECT_INFO TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYS.V_$VERSION TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_ADMIN_LICENSES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_FU_LICENSE_MAP TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_FU_REGISTRATIONS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_FU_STATISTICS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_INV_COMPONENT TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_INV_CONTAINER TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_LICENSE_CONFIRMATION TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_LICENSE_DEFINITIONS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_LICENSED_TARGETS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_LICENSES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_TARGET_TYPES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_TARGETS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSMAN.MGMT_VERSIONS TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSTEM.AQ$_QUEUE_TABLES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSTEM.AQ$_QUEUES TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSTEM.FND_ORACLE_USERID TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON SYSTEM.PRODUCT_PRIVS TO C##OSCAN WITH GRANT OPTION CONTAINER=ALL;
GRANT SELECT ON SYSTEM.SCHEMA_VERSION_REGISTRY TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON TIMESTEN.TT_GRIDID TO C##OSCAN CONTAINER=ALL;
GRANT SELECT ON TIMESTEN.TT_GRIDINFO TO C##OSCAN CONTAINER=ALL;
These privileges allow Snow Inventory Oracle Scanner to read metadata about database objects, but not the data inside them. They are needed in order to determine the license needs; if there for example exists partitioned or compressed tables.
If E-Business Suite scanning is enabled, the following example adds the required Oracle permissions for the user C##OSCAN. Make sure you are executing the example script from the container (pluggable database) that contains the E-Business Suite schema. The default database schema for Oracle E-Business Suite is APPS. If you configured E-Business Suite on another database schema, make sure to apply the proper schema name on the example script as well.
GRANT SELECT ON APPS.AD_APPLIED_PATCHES TO C##OSCAN;
GRANT SELECT ON APPS.FND_APPLICATION TO C##OSCAN;
GRANT SELECT ON APPS.FND_APPLICATION_TL TO C##OSCAN;
GRANT SELECT ON APPS.FND_FORM_FUNCTIONS TO C##OSCAN;
GRANT SELECT ON APPS.FND_FORM_FUNCTIONS_TL TO C##OSCAN;
GRANT SELECT ON APPS.FND_LOGIN_RESPONSIBILITIES TO C##OSCAN;
GRANT SELECT ON APPS.FND_LOGINS TO C##OSCAN;
GRANT SELECT ON APPS.FND_MENU_ENTRIES TO C##OSCAN;
GRANT SELECT ON APPS.FND_MENU_ENTRIES_TL TO C##OSCAN;
GRANT SELECT ON APPS.FND_MENUS TO C##OSCAN;
GRANT SELECT ON APPS.FND_MENUS_TL TO C##OSCAN;
GRANT SELECT ON APPS.FND_PRODUCT_INSTALLATIONS TO C##OSCAN;
GRANT SELECT ON APPS.FND_RESP_FUNCTIONS TO C##OSCAN;
GRANT SELECT ON APPS.FND_RESPONSIBILITY TO C##OSCAN;
GRANT SELECT ON APPS.FND_RESPONSIBILITY_TL TO C##OSCAN;
GRANT SELECT ON APPS.FND_SECURITY_GROUPS TO C##OSCAN;
GRANT SELECT ON APPS.FND_USER TO C##OSCAN;
GRANT SELECT ON APPS.FND_USER_RESP_GROUPS TO C##OSCAN;
GRANT SELECT ON APPS.FND_USER_RESP_GROUPS_ALL TO C##OSCAN;
GRANT SELECT ON APPS.FND_USER_RESPONSIBILITY TO C##OSCAN;
GRANT SELECT ON APPS.ICX_SESSIONS TO C##OSCAN;
GRANT SELECT ON APPS.OE_ORDER_HEADERS_ALL TO C##OSCAN;
GRANT SELECT ON APPS.OE_ORDER_LINES_ALL TO C##OSCAN;
GRANT SELECT ON APPS.OE_ORDER_SOURCES TO C##OSCAN;
GRANT SELECT ON APPS.WF_LOCAL_USER_ROLES TO C##OSCAN;
GRANT SELECT ON APPS.WF_USER_ROLE_ASSIGNMENTS TO C##OSCAN;
GRANT SELECT ON APPS.PER_ALL_PEOPLE_F TO C##OSCAN;
GRANT SELECT ON APPS.HR_LEGISLATION_INSTALLATIONS TO C##OSCAN;
GRANT SELECT ON APPS.FND_PROFILE_OPTIONS TO C##OSCAN;
GRANT SELECT ON APPS.FND_PROFILE_OPTION_VALUES TO C##OSCAN;
GRANT SELECT ON APPS.FND_NODES TO C##OSCAN;
GRANT SELECT ON APPS.FND_PRODUCT_GROUPS TO C##OSCAN;
GRANT SELECT ON APPS.AP_INVOICES_ALL TO C##OSCAN;
GRANT SELECT ON APPS.PER_CONTRACTS_F TO C##OSCAN;
GRANT SELECT ON APPS.PER_PERSON_TYPES TO C##OSCAN;
GRANT SELECT ON APPS.BEN_PRTT_ENRT_RSLT_F TO C##OSCAN;
GRANT SELECT ON APPS.CN_SRP_PLAN_ASSIGNS_ALL TO C##OSCAN;
GRANT SELECT ON APPS.PO_REQUISITION_HEADERS_ALL TO C##OSCAN;
GRANT SELECT ON APPS.PO_REQUISITION_LINES_ALL TO C##OSCAN;
GRANT SELECT ON APPS.PER_ADDRESSES TO C##OSCAN;
GRANT SELECT ON OTA.OTA_DELEGATE_BOOKINGS TO C##OSCAN;
GRANT SELECT ON APPS.HXC_TIMECARD_SUMMARY TO C##OSCAN;
GRANT SELECT ON APPS.HXC_TIME_BUILDING_BLOCKS TO C##OSCAN;
GRANT SELECT ON APPS.POA_EDW_PO_DIST_F TO C##OSCAN;
GRANT SELECT ON APPS.PER_PERSON_TYPES_TL TO C##OSCAN;
GRANT SELECT ON APPS.PER_PERSON_TYPE_USAGES_F TO C##OSCAN;
GRANT EXECUTE ON APPS.QP_UTIL TO C##OSCAN;
GRANT EXECUTE ON APPS.HR_PERSON_TYPE_USAGE_INFO TO C##OSCAN;
Database vault
When Database Vault is enabled, then SYS or the specific Oracle user must:
-
have PARTICIPANT or OWNER authorization on 'Oracle Data Dictionary" realm
-
have PARTICIPANT or OWNER authorization on 'Oracle Database Vault' realm
-
be granted the DV_SECANALYST role for querying Oracle Database Vault-supplied views
-
be granted SELECT on LBAC$POLT from LBACSYS
Example: Database Vault
Example using OSCAN.
Log into the database instance as a user who has been granted the DV_OWNER or DV_ADMIN role.
sqlplus /nolog
conn DV_OWNER/<password>
grant DV_SECANALYST to OSCAN;
exec DVSYS.DBMS_MACADM.ADD_AUTH_TO_REALM('Oracle Data Dictionary','OSCAN');
exec DVSYS.DBMS_MACADM.ADD_AUTH_TO_REALM('Oracle Database Vault','OSCAN');
conn LBACSYS/<password>
grant select on LBACSYS.LBAC$POLT to OSCAN;